What is a double-spend?
Double spending is done when the same money is spent more than once. This term is used exclusively for digital money - in the sense that you would have a hard time spending the same physical money twice. When you pay for coffee these days, you hand the cash to the cashier, who probably puts it in the cash register. You can't go to the coffee shop across the street and buy another coffee with the same bill.
In digital money circuits, there is a possibility that you may be able to do this. You've probably already copied and pasted a computer file. You can email the same file to ten or more people.
If digital money is just data, you need to prevent the same units from being copied and spent in different places. Otherwise your currency will collapse in seconds.
Why is Proof of Work required?
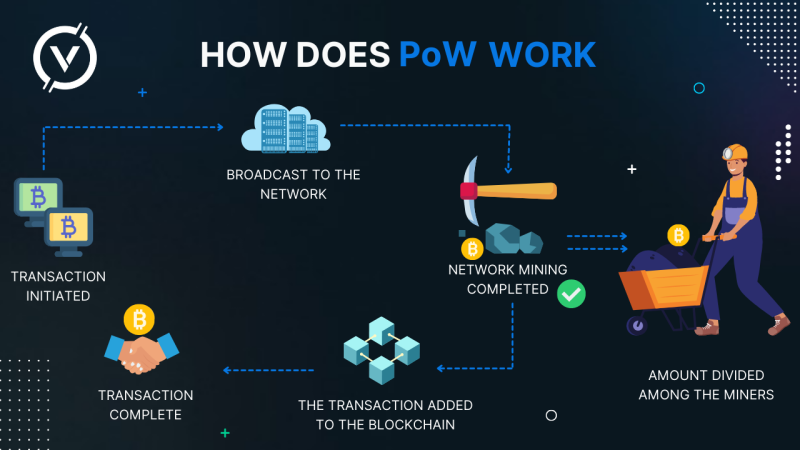
Users broadcast transactions to the network. Transaction confirmation occurs when miners create a new block in the network every ten minutes . They compete to see if their local block will become the next block in the chain for the entire network.
Blockchain is a large database available to everyone, allowing you to check whether funds have been spent before. For example: you and three friends have a notepad. Every time one of you wants to transfer some units, you write it down - Mary pays Pete five units, Pete pays Elena two units, etc.
There is another nuance here - every time you make a transaction, you are referring to the transaction where the funds are from. So, if Pete pays Elena with two units, the entry would look like this: Pete pays Elena two units from a previous transaction with Mary.
That way, we have the ability to keep track of the units. If Pit makes another transaction using the same units he just sent to Elena, everyone will understand it right away. The group will not let the transaction to be written to the notepad.
Such a scheme might work well for a small group. Everyone knows each other, so they will probably agree on which friend will add transactions to the notepad. However this idea doesn't work very well for large-scale projects, because no one wants to trust a stranger to manage it.
This is where Proof of Work enters the picture. It ensures that users do not spend money they are not entitled to. The PoW algorithm, based on a combination of game theory and cryptography, allows each user to make changes to the blockchain according to the rules of the system.
How does PoW work?
Let's go back to our notebook. Think of it as a blockchain.But transactions are not added one by one - instead they are combined into blocks. We declare transactions on the network, and then the users creating the block include them in the block candidate. Transactions will only become valid once the candidate block has become a confirmed block, in other words, has been added to the Block.
Appending a block, however, does not come cheap. Proof of Work requires the miner (the user creating the block) to use some of their own resources to gain an advantage. Proof-of-work requires the miner (the user creating the block) to use some of their own resources to gain an advantage. These resources are the processing power used to hash the block data until then.
If the resulting hash value meets the constraints then the hash puzzle is solved, otherwise the computation must continue with another one-time random code until a solution is found.
Hashing block data means that you pass it through a hashing function to create a block hash. A block hash acts like a "fingerprint" - it is an identifier of your input data and is unique to each block.
Changing the block hash back to receive the input data is almost impossible. However, knowing the input data, it is easy to make sure that the hash is correct.
It is enough to pass the input data through the function and verify that the result is identical.
In Proof of Work, you must specify data whose hash conforms to certain rules set out in the protocol. However, you do not understand how to achieve this. Your only option is to run the data through a hash function and see if it matches the terms. If it doesn't, you'll need to change the data a bit to get another hash. Changing even one character in your data will lead to a completely different result, so it is impossible to predict what the final output might be.
As a result, if you want to create a block, you just guess. Normally you take the information about all the transactions you want to add, and some other important data, and then hash all that together.
But because your data set won't change, you need to add some of the information, which is variable. Otherwise you will always get the same hash in the output. This variable data is called a nonce. It's a number that you will change on every try, so that you will get a different hash each time. This is what is called mining.
So mining is the process of collecting blockchain data and hashing it together with a one-time code until you find a suitable hash. If you find a hash that meets the conditions set by the protocol, you are allowed to broadcast the new block into the network. At this point, the other participants in the network need to update their blockchains to include the new block.
Currently, for major cryptocurrencies, these conditions are incredibly difficult to meet. The higher the hash rate, the more miners are involved in mining, the less time they need to find the blocks - complexity increases; the lower the hash rate, the fewer miners, the more time is spent mining - complexity decreases.
As you can imagine, trying to guess a huge number of hashes can be detrimental to your computer. You waste computational cycles and energy. You waste computational cycles and energy. However, it will reward you with cryptocurrency if you find the right hash.
Let us briefly describe what is known today:
- Mining is expensive
- You get income if you mine a valid block
- Knowing the input data, the user can easily verify its hash - non-mining users can verify the validity of the block without much computational effort.
So, everything is great. But what if someone wants to cheat? It is possible to put a bunch of fake transactions into a blockchain and get a true hash.
This is where public key cryptography helps. In brief, it uses some clever cryptographic techniques. This way, any user can check whether someone has the right to transfer the funds they want to spend.
When a user creates a transaction and signs it, anyone on the network can see your digital signature and compare it with the data on your public key. They will also check that you really don't spend more than you actually have.
An invalid block will be rejected. Naturally, the block is as valid as the transactions it contains. Even a simple attempt at fraud will cost you dearly. You will be wasting your own resources without any refund.
This is the essence of Proof of Work: fraud costs dearly, while honest activity makes a profit. Any reasonable miner will seek a return on investment, so you can expect them to act in a way that generates a steady income.
Proof of Work or Proof of Stake
One of the most promising consensus algorithms is Proof of Stake (PoS). This model appeared back in 2011 and has been applied to some small protocols. However, it has yet to gain acceptance in any of the larger blockchains.
Proof of stake (PoS):
This protocol makes the entire mining process virtual. In such a system, miners take the place of validators. The process looks like this: first you, as a validator, need to block some of the ethers you own as a share. After that, you can validate the blocks. This means that if you find a block that you think should be included in the blockchain, you can validate it by putting your share on it. There is no mining here, nor is there a race to guess hashes. Instead, the users are randomly selected - if selected, they must offer (or " forge") a block. When a block is valid, they will get a reward consisting of the transaction fees from that block.
However, not every user can be chosen - they are selected by the protocol based on a variety of factors. To participate, you need to fix a bet,which is a predetermined amount of money in your own blockchain currency. If they act dishonestly, their stake (or part of it) will be withdrawn.
Proof of Stake has some advantages. The most notable of these is the lower carbon dioxide emissions. Due to the fact that PoS does not require powerful mining systems, the electricity consumed is only a fraction of that consumed in PoW.
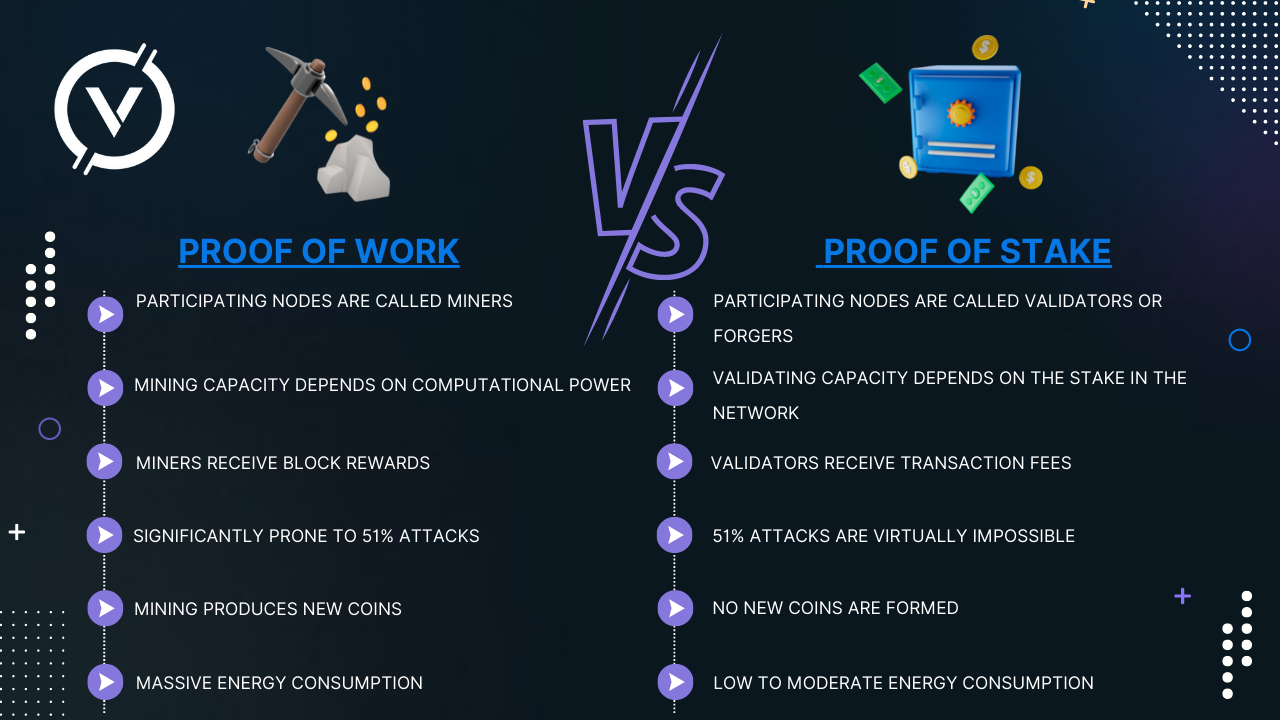
Despite this, its history is nothing compared to that of PoW. Although mining may be perceived as a waste of money, it is mining that is considered the only consensus algorithm that is truly effective. It has protected trillions of dollars worth of transactions in just a decade. To claim with certainty whether PoS can compete with it in terms of reliability and security mining must be tested in the wild.
Final Thoughts
The idea of proof-of-stake is to solve the problem of proof-of-work associated with high electricity consumption. Proof-of-stake is also a robust and secure blockchain consensus mechanism. double spending is the repeated (sometimes multiple) sale of the same funds. Bitcoin has been able to survive and evolve to where it is today because it has reduced the likelihood of the 'double spending' problem.
Using cryptography, hash functions, and game theory, users in a decentralized environment can negotiate the state of the financial database.